Stored XSS in Google Drive

Here is a vulnerability i discovered in Google Drive
[ drive.google.com – docs.google.com ]
Stored XSS vulnerability in Google Drive [Folder name]
In Google drive, I created a folder with this name:
‘”><svg/onload=prompt(1337)>
then searched about any place which need writing my folder name in the page
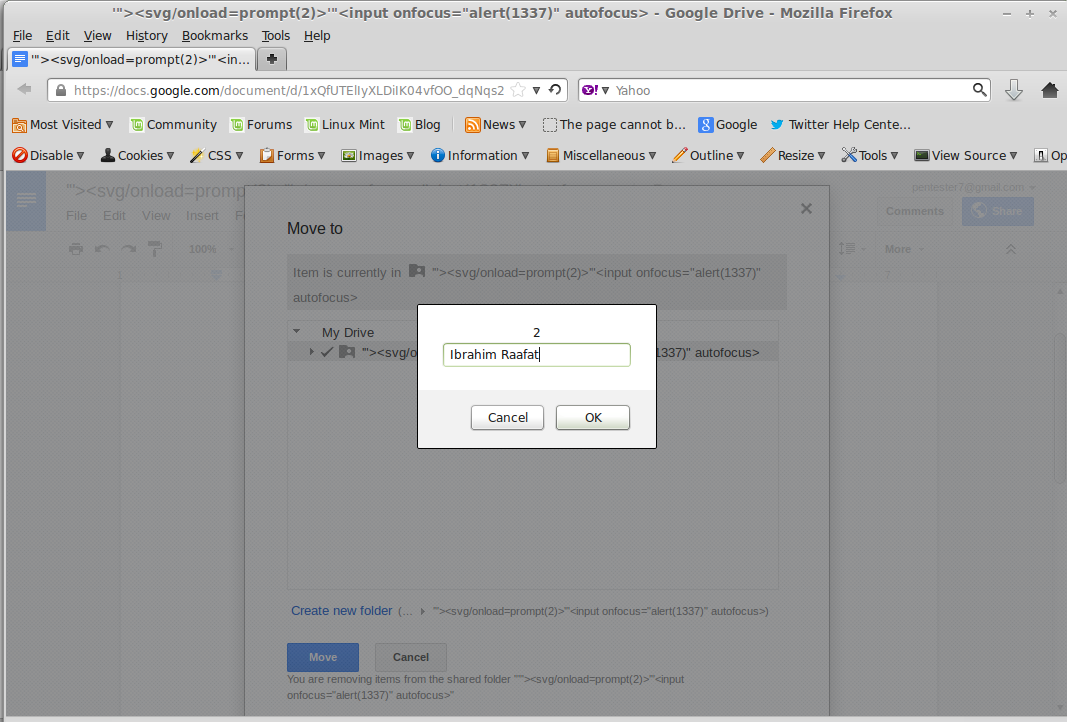
I found that i can move my documents to a folder
So i moved it and my document now in my Folder -> ‘”><svg/onload=prompt(1337)>
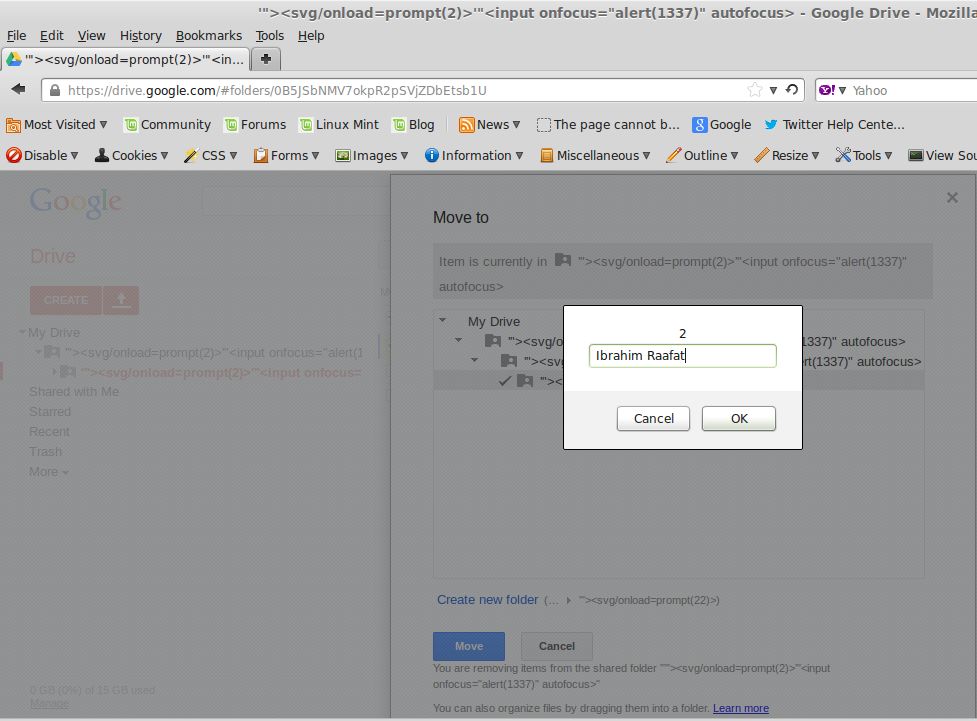
I created another folder name, as example: folder name is “Folder2”
I moved the document to the other folder -> “Folder2”
The code executed successfully
Why?
In the normal case, after i click on Move to folder, i should get this message
“Other users will no longer see this item in shared folder $currentfoldername“
And my current Folder name was : ‘”><svg/onload=prompt(1337)>
That’s why i moved the document two times,
First time: to make the current folder name is my payload and the second time to execute it
Thus, The final result was my PROMPT and this message after it
Other users will no longer see this item in shared folder ‘”>
This code executed <svg/onload=prompt(1337)>
By sharing the folder to the victim, Attacker can execute the vulnerability on user if he tried to move it to another folder
Video: http://www.youtube.com/watch?v=jvswssiXw0A
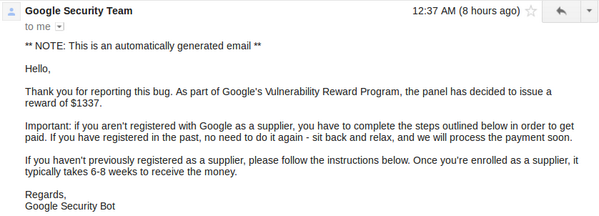
Bounty: $1337
Quote of the day
N/A




Wow.. amazing, dude!
Have a nice day, sit back and relax! 😀
@R-ID
Thanks bro =))
Mil gracias
Ooops! that’s a good one! Congratulations ,bro. 🙂
ابعتل للGoogle Security Team قولهم “العيب في النظام يا بهايم” -برايز 😀
@Jose Thanks
@Ahmed Elsobky hhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh, Kont 3awez a7otha 😀
http://photos-a.ak.fbcdn.net/hphotos-ak-ash3/602857_666258106759346_442267110_n.jpg 😀
Pingback: พบบั๊ก XSS ใน Google Drive, นักวิจัยอียิปต์รับรางวัล 1337 ดอลลาร์
Why did you need to do it twice if the script executed both times?
@N00b If you are talking about the video, I just did it twice for the viewers, when you see it two times it will be better than replaying the video again =))
Nice $1337 bounty 😀