Deutsche Telekom Database Dump
Here is a simple and critical vulnerability I’ve found in Deutsche Telekom allowed me to dump the database due to Authorization bypass.
The web application main page is the login page: demandplan.telekom.de/identification.php
I opened the web page source and there were some php file names inside javascript such as
index.php, adminuser.php, ProjectExport.php and so on..
I tried to browse every file, all of them redirected to the login page, But that ProjectExport.php file took more seconds and then redirected to the login page.
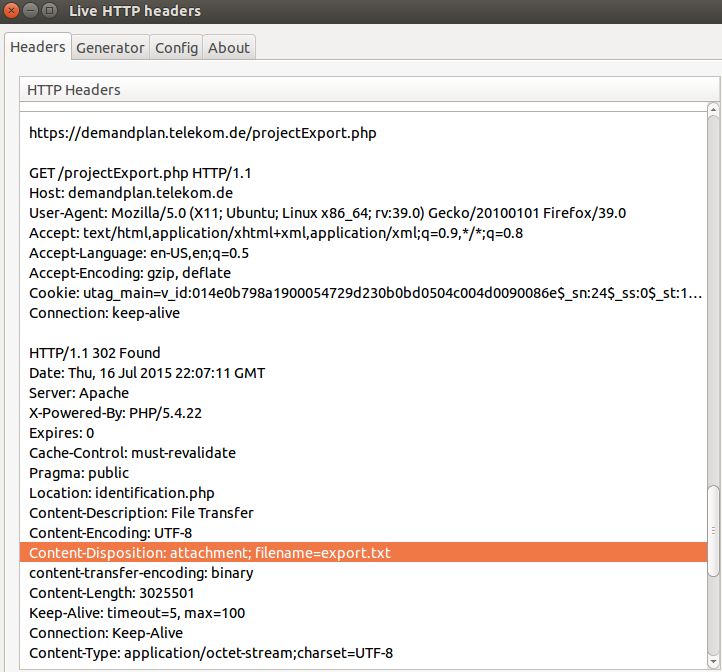
https://demandplan.telekom.de/projectExport.php
More seconds with file name includes “export” referred that there is something happened, I opened the file again and I found what I expected, Content-Disposition header response included an attached file -> “export.txt”
This file generated a backup file of the database
By intercepting the response, the generated file content open in the response body, Check the Content-Length header.
That’s enough to get the data but I wanted to get the exact folder name, https://demandplan.telekom.de/$foldername/export.txt
Via a simple manual bruteforce I got it => /export
Final file path was: https://demandplan.telekom.de/export/export.txt
That file included a backup of the database.
Auth Bypass:
Admin login and privileges validation should happen before opening the web page content, Not after, In this web app, the page content opened then validation happened which resulted in redirection to the login page, Just stop the redirection and act like admin.
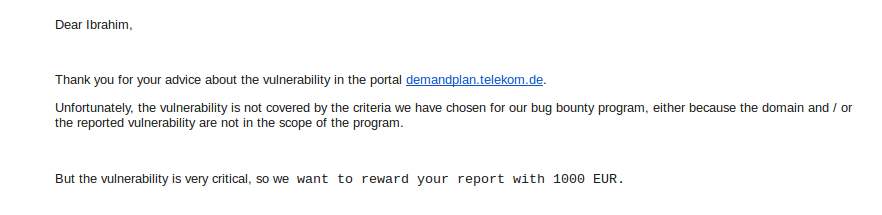
Telekom only rewards SQLI or RCE reports, But they rewarded this one with 1000 Euro as it’s a very critical one.
Thanks Telekom